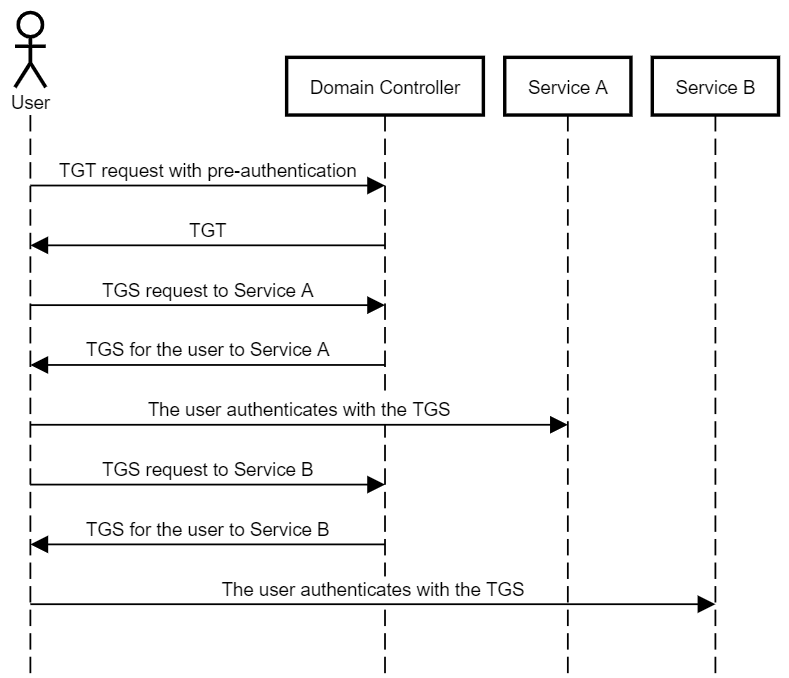
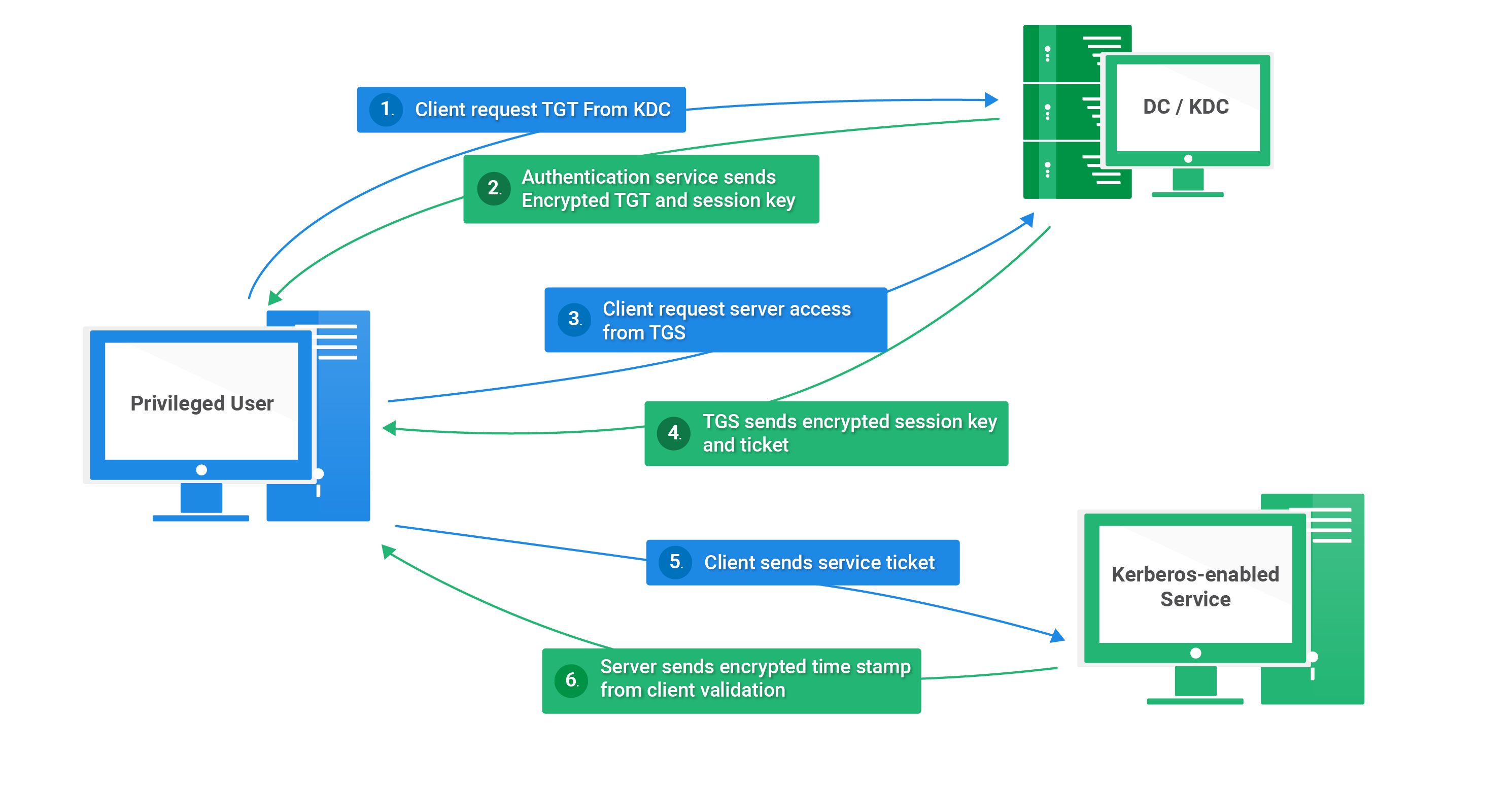
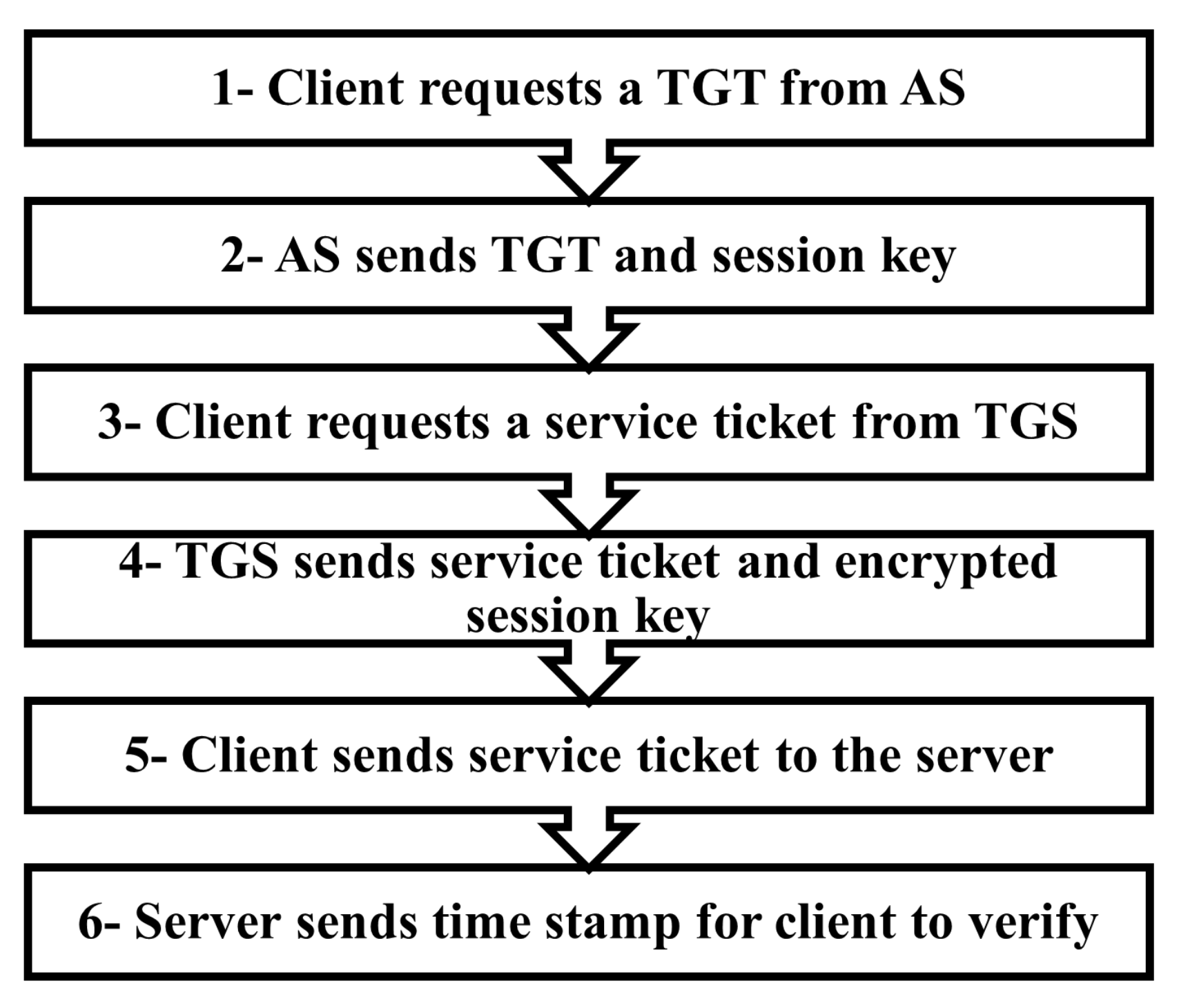
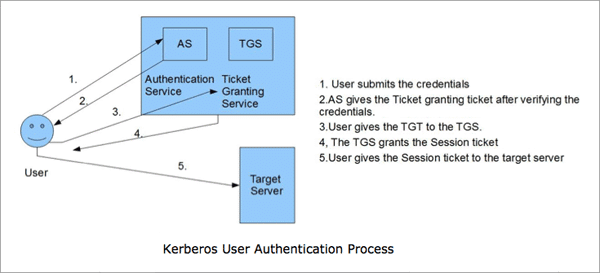
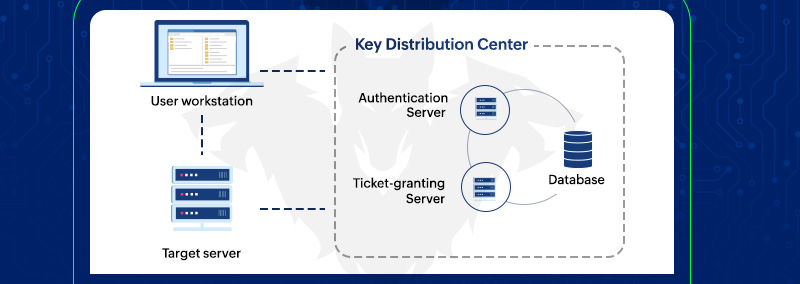
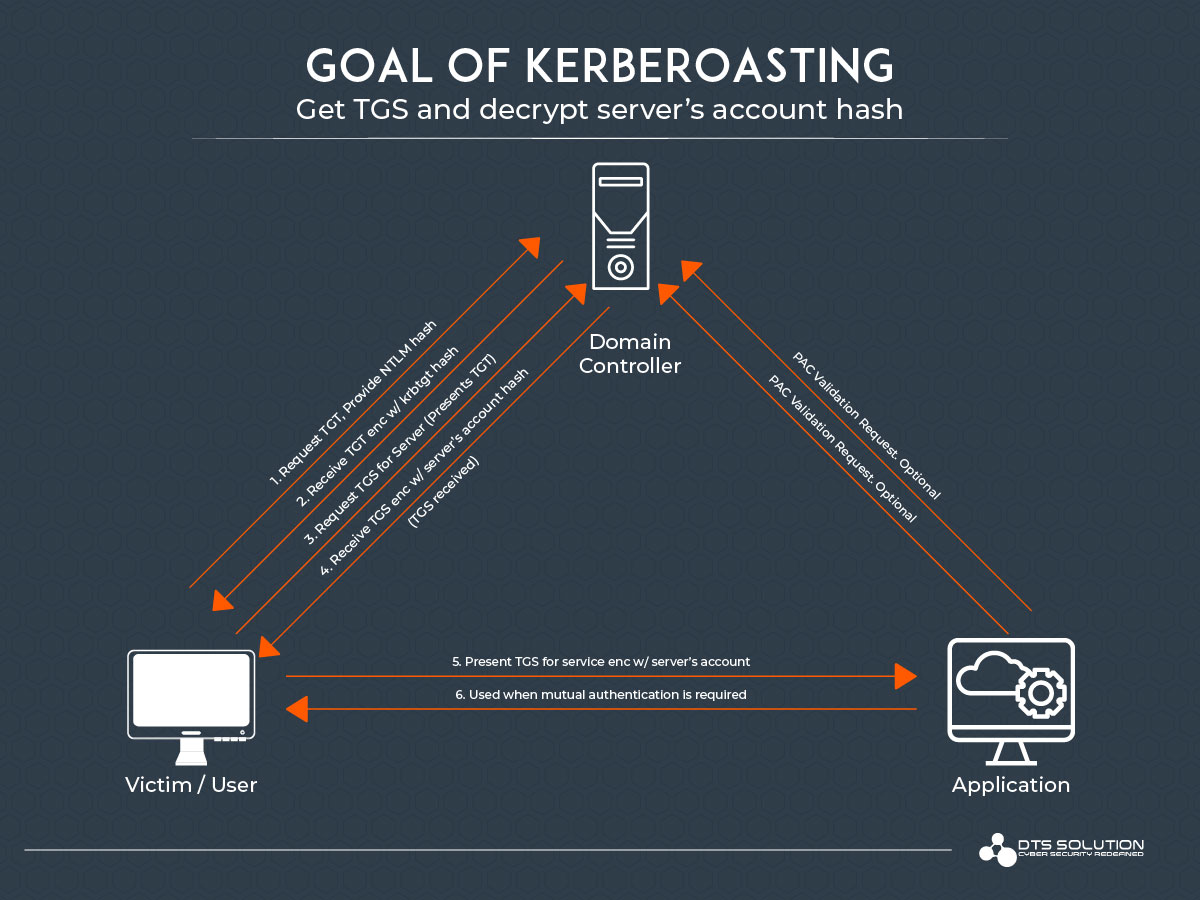
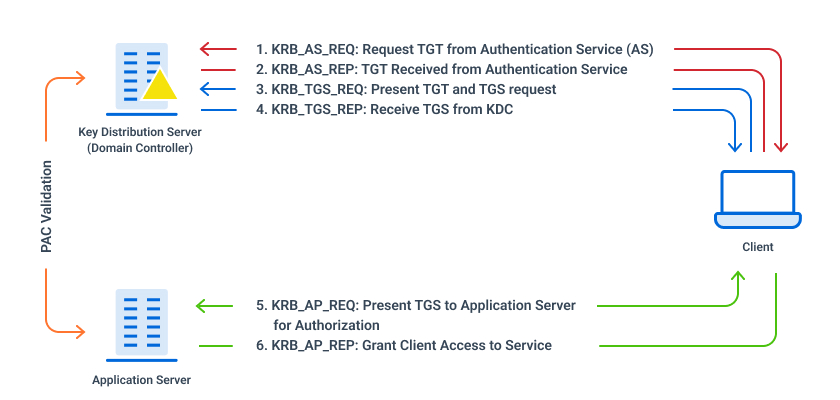
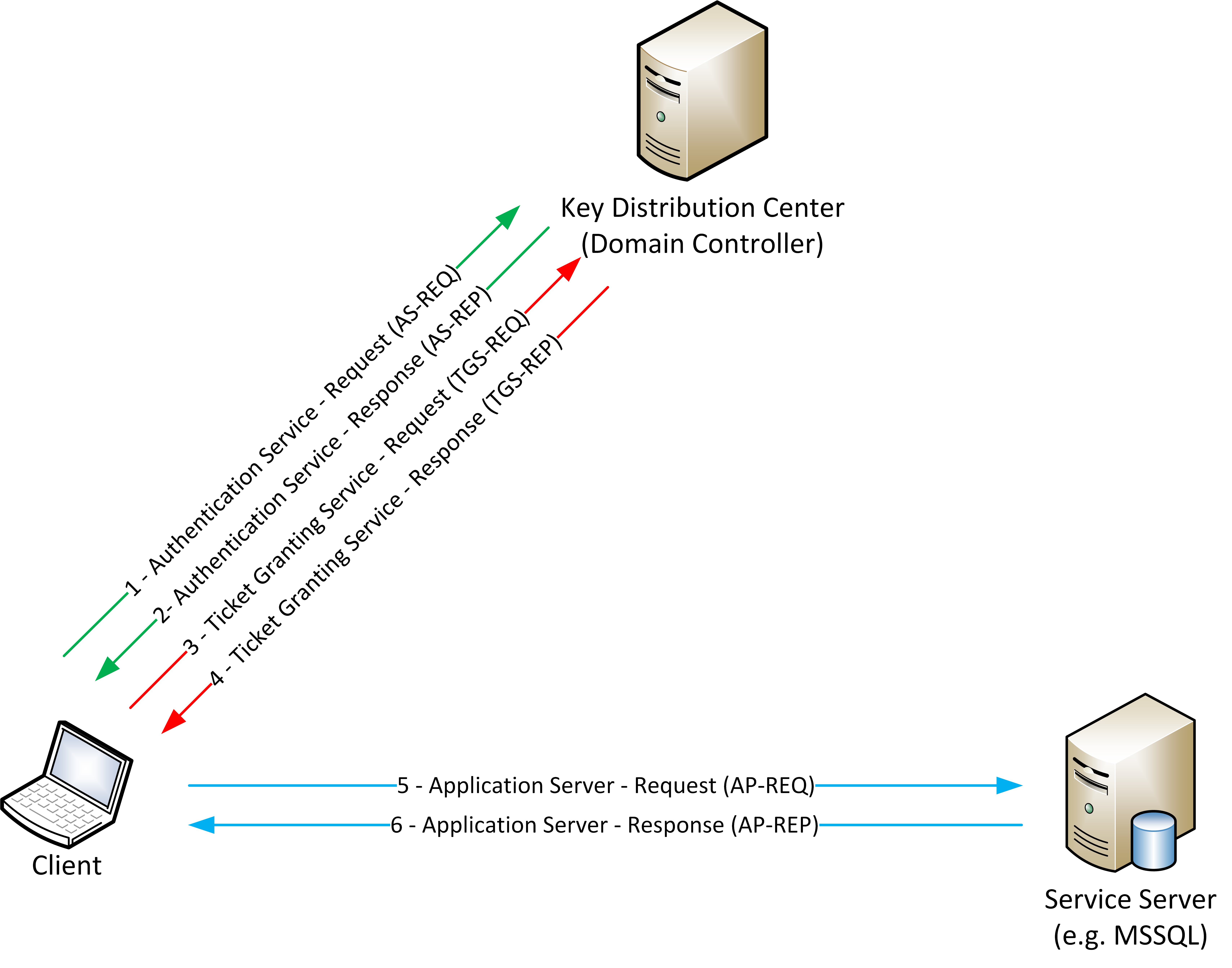
active directory Kerberoasting – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis

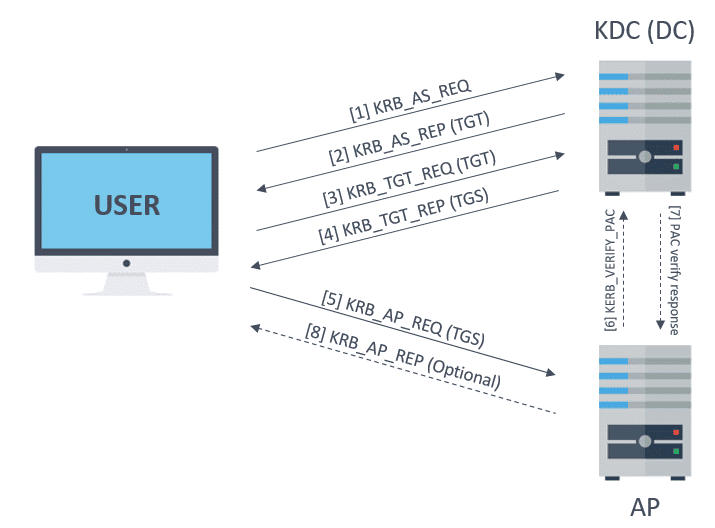
active directory Kerberoasting – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis
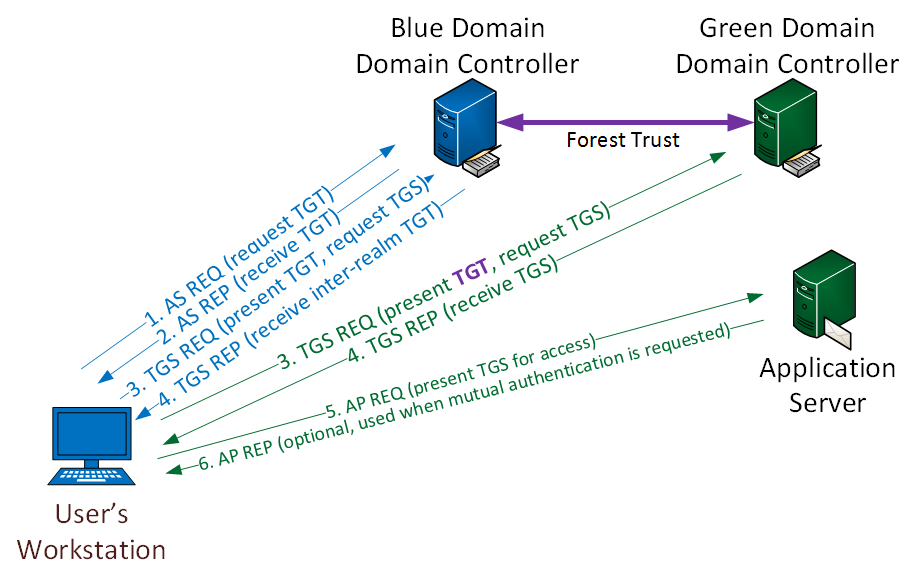
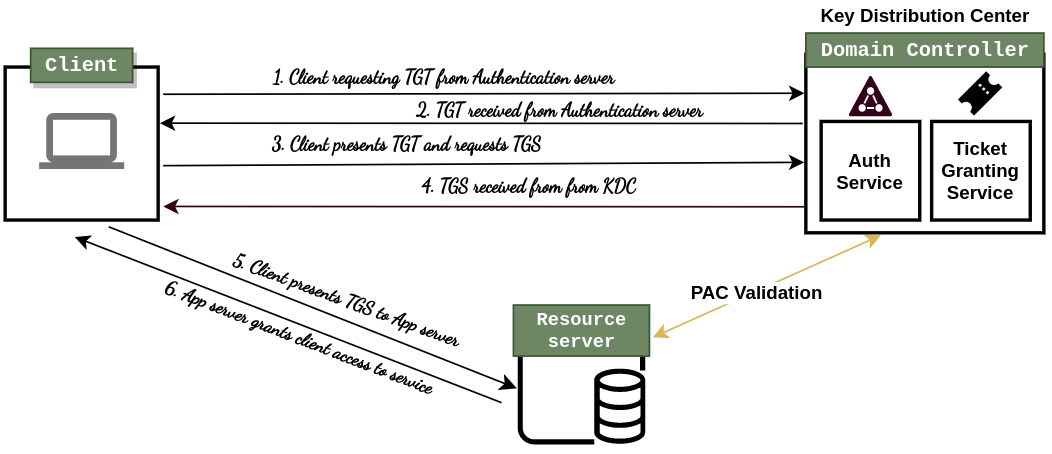
It's All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts » Active Directory Security
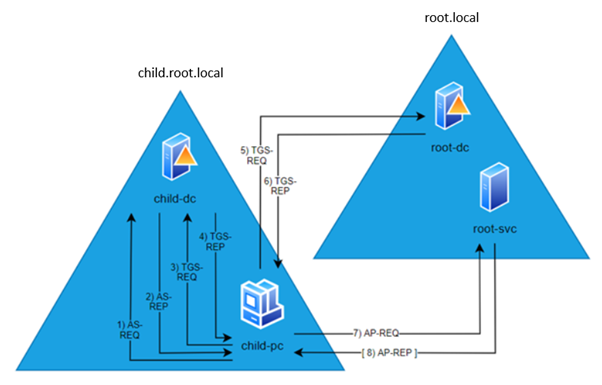
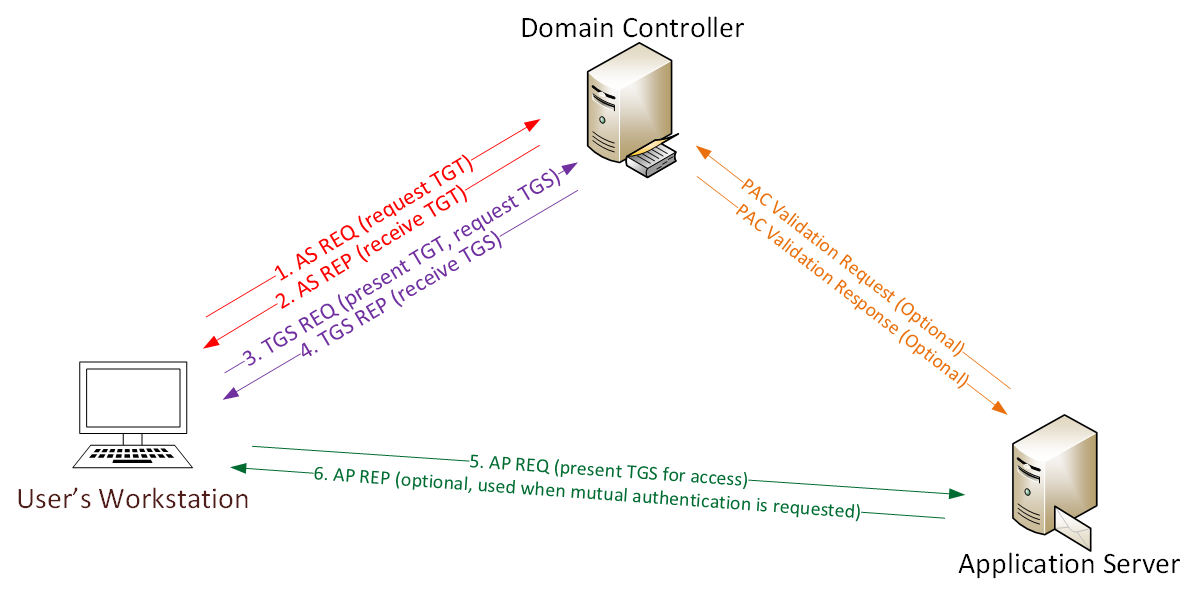
SID filter as security boundary between domains? (Part 1) - Kerberos authentication explained — Improsec | improving security

Enabling Single Sign On into SAP using Microsoft proprietary Windows Kerberos authentication(GSS-API) | SAP Blogs