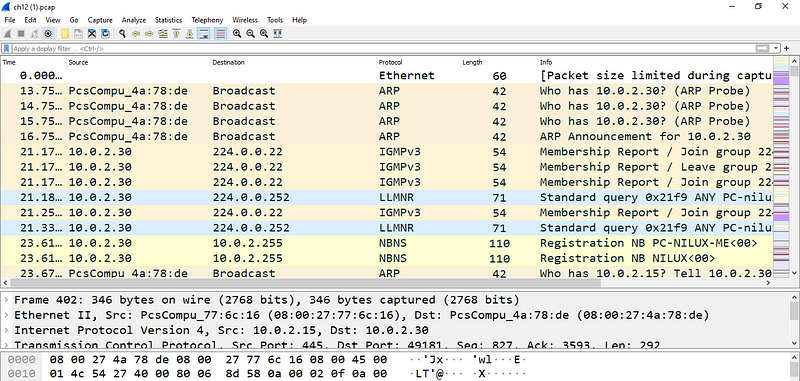
ADTimeline – Active Directory forensics with replication metadata at the FIRST Technical Colloquium | Agence nationale de la sécurité des systèmes d'information
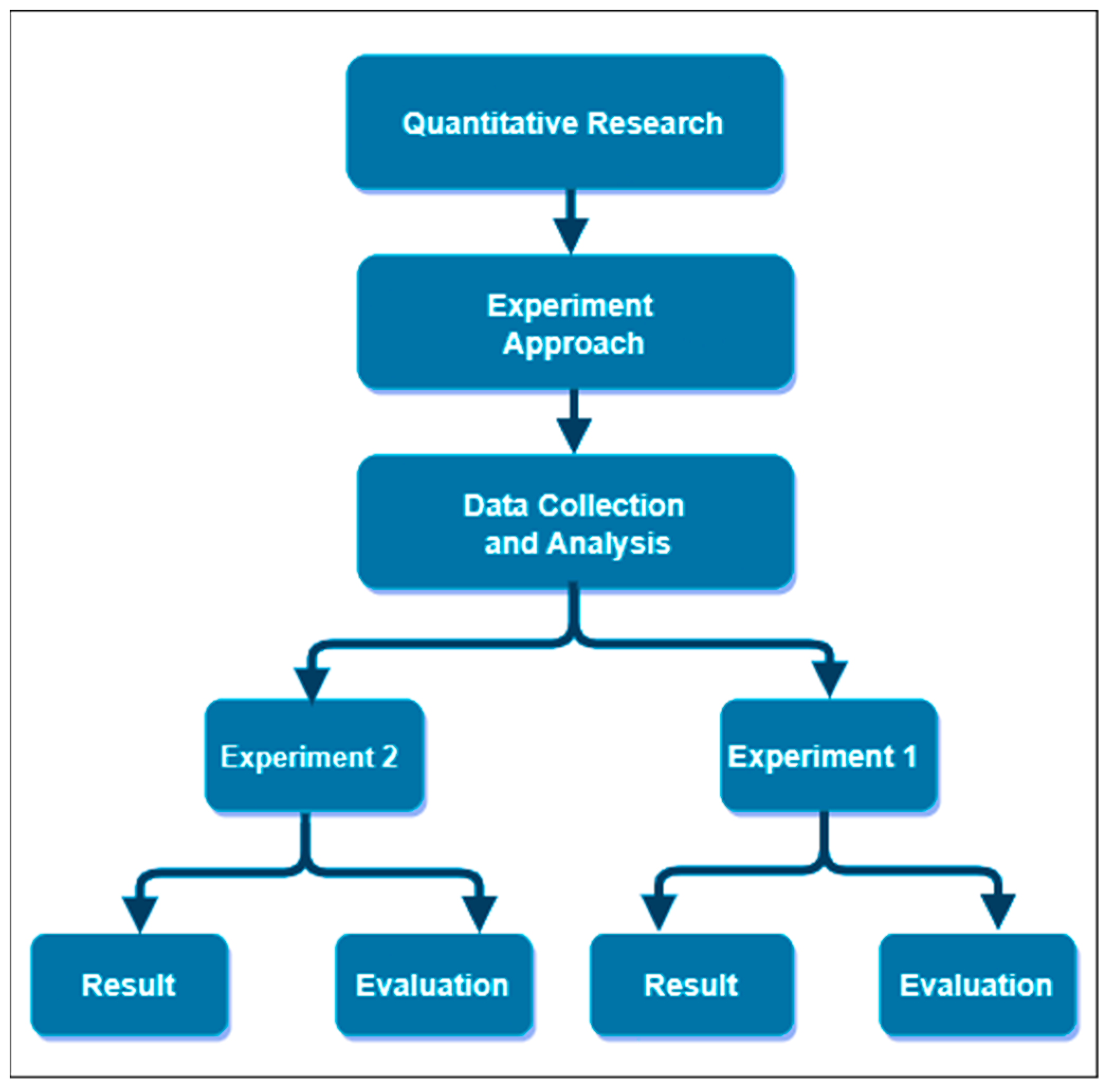
Future Internet | Free Full-Text | Exploiting Misconfiguration Vulnerabilities in Microsoft’s Azure Active Directory for Privilege Escalation Attacks
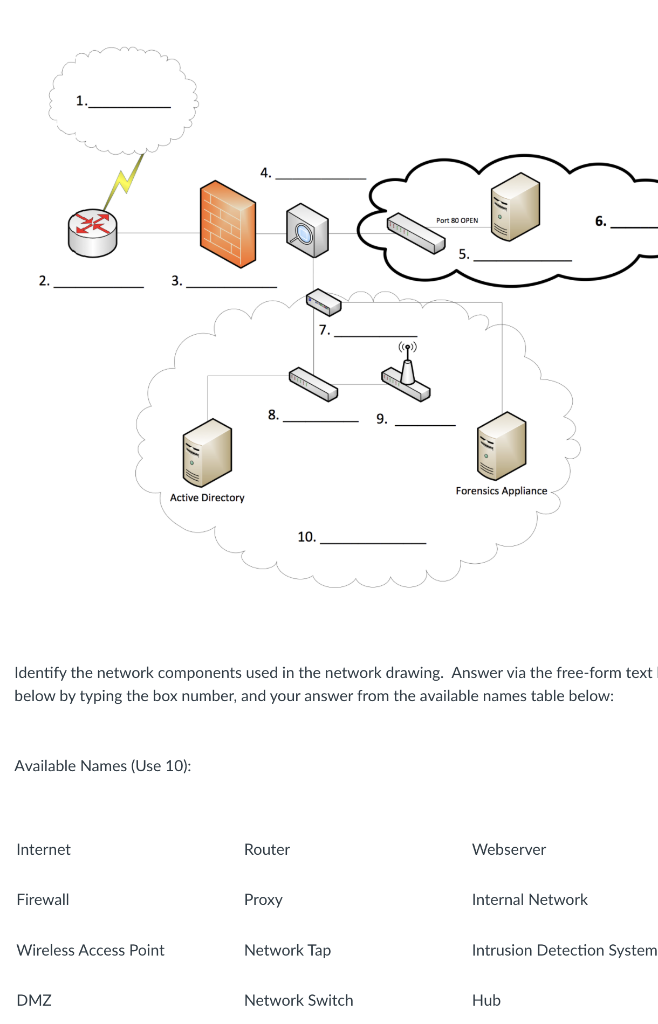
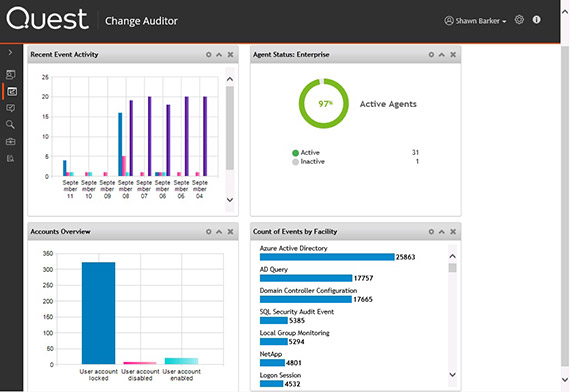
Cyber Forensics - Active Directory Investigation - Cyber Security Blogs - Cyber Forensics - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata

Semperis is the only company 100% focused on cyber protection, detection and cyber recovery of Active Directory with purpose built technology...